Domain Admins.
We also recommend following the article SharpHound Enterprise Service Hardening.
AD Structure Data
By default, allAuthenticated Users may query data from Active Directory via LDAP. Unless modifications have been made to this default, administrative privilege is not required for SharpHound to collect AD Structure Data.
Restricted Read Permissions
If modifications exist that restrict the default read permissions, the SharpHound collector service account must be a member of an audit role group which is grantedRead Property and Read Permissions on all collected AD objects.
Deleted Objects Container (Optional)
SharpHound can read the content of the Deleted Objects container (also known as the AD Recycle Bin). Collecting deleted objects affects data retention behavior in BloodHound Enterprise, see Active Directory Recycle Bin for details on how this impacts retention periods. You can delegate permissions to a group for read access to the “Deleted Objects” container, and then add the SharpHound collector service account to that group. The Deleted Objects container locations are:- Domain NC Deleted Objects DistinguishedName (DN):
CN=Deleted Objects,<Domain DN> - Configuration NC Deleted Objects DistinguishedName (DN):
CN=Deleted Objects,CN=Configuration,<Forest root domain DN>
SharpHound can read these containers even if the AD Recycle Bin feature is not enabled.
Local Group Membership
SharpHound collects local group membership via Remote SAM Enumeration. By default, on currently supported Windows operating systems, onlyAdministrators on the device(s) being collected have this right on Windows clients and member servers. For compatibility purposes, Everyone is granted this right on domain controllers by default.
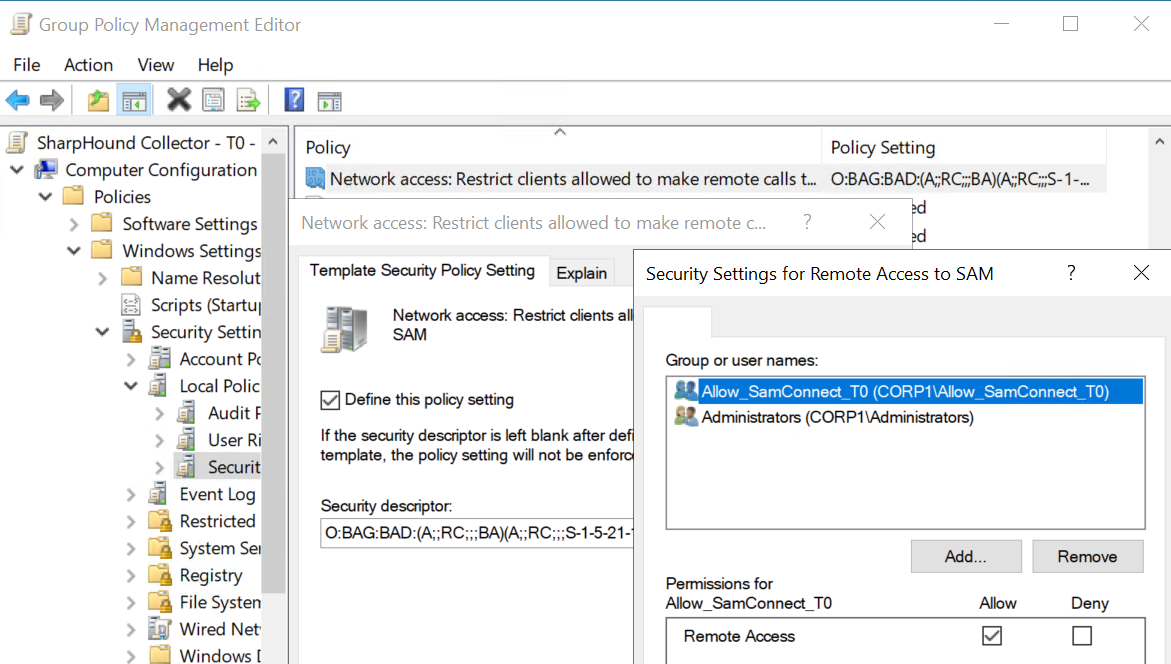
Microsoft supports delegating this permission via a properly scoped Group Policy Object with the Network access: Restrict clients allowed to make remote calls to SAM setting.
For example, if our Tier Zero SharpHound collector gMSA is a member of the Allow_SamConnect_T0 group, a GPO configured like this and linked to the Tier Zero OU where all of the non-DC Tier Zero assets are located, SharpHound will be able to collect Local Group data from those hosts.
User Rights Assignments
OnlyAdministrators can perform the LsaOpenPolicy and LsaEnumerateAccountsWithUserRights function calls necessary to collect User Rights Assignments (URAs) directly from a remote host. There is no known way around this limitation.
Currently, not collecting User Rights Assignments may cause inaccurate CanRDP edges. In the future, SharpHound may collect additional user rights to identify more attack paths.
Sessions
By default, localAdministrators have the rights necessary to perform the NetWkstaUserEnum function calls to collect session data.
While not ideal, local Print Operators also have the rights necessary to collect session data from Windows Server hosts. Unfortunately, this option does not exist on Windows desktop operating systems. An alternate collection method, such as event log parsing, is required to collect session data from all domain-joined devices.
To collect session data from domain controllers, the collector service account can be added to the local builtin Print Operators group for the domain. When doing this it is also important to lessen the capabilities of the Print Operators group by removing the default User Rights Assignments created by the Default Domain Controllers Policy linked to the Domain Controllers OU. The Print Operators group should no longer be granted rights to Allow log on locally: SeInteractiveLogonRight, Load and unload device drivers: SeLoadDriverPrivilege, and Shut down the system: SeShutdownPrivilege. Domain controllers should not be used as print servers and the builtin Print Operators group for the domain should be unused, except perhaps for this purpose.
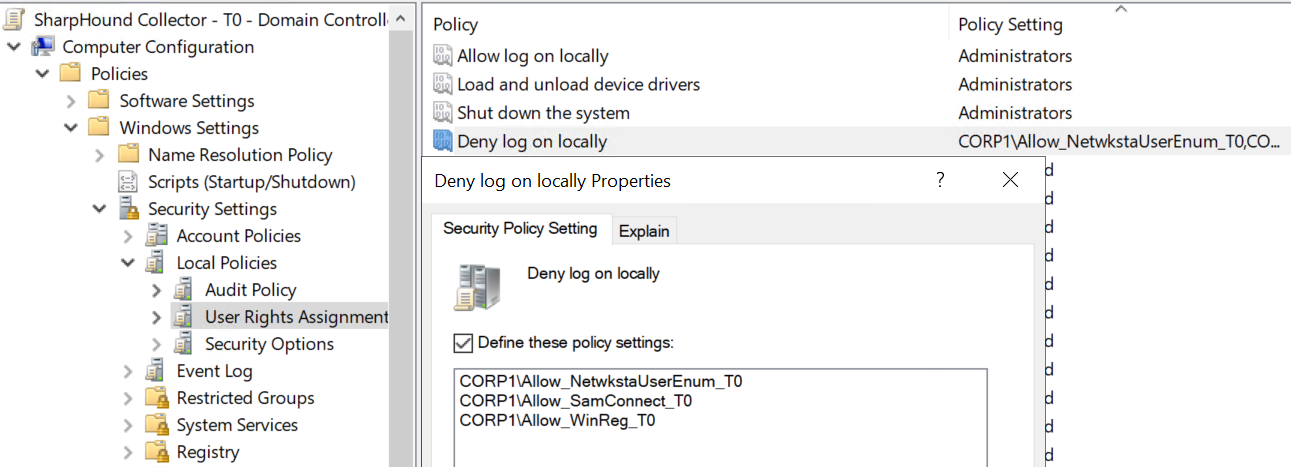
Print Operators group on each device. The best way to accomplish this is likely via Group Policy Preferences.
For example, if our Tier One SharpHound collector gMSA is a member of the Allow_NetwkstaUserEnum_T1 group, a GPO configured like this and linked to any OUs where Tier One assets are located will grant the SharpHound collector session enumeration rights.
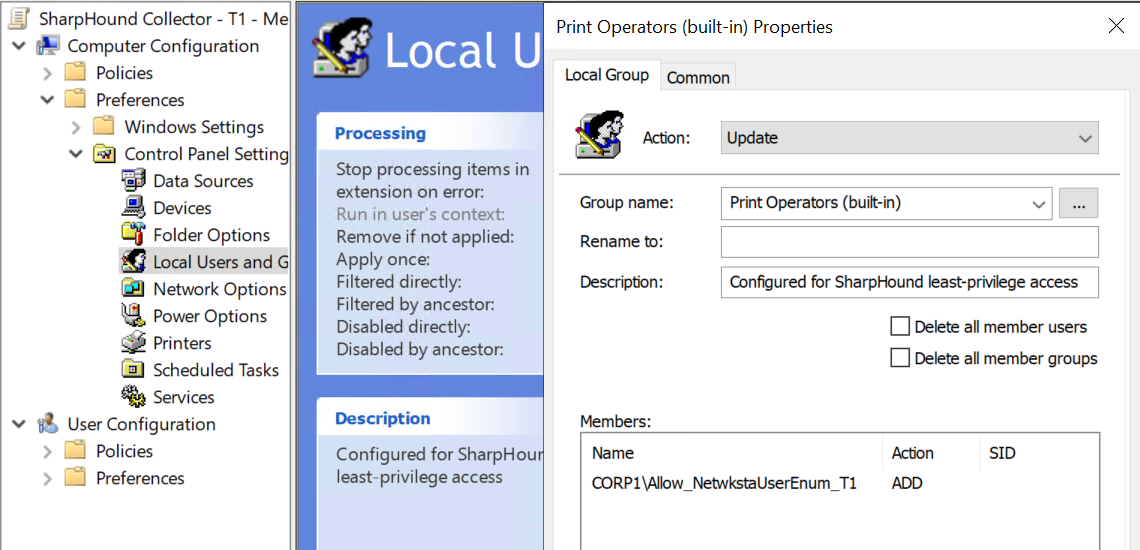
Administrators group on each endpoint, which is best handled via Group Policy Preferences. Utilizing a service account that is a member of Domain Admins is strongly discouraged.
There may be other options for collecting session data from the environment, such as parsing Windows event logs from all forest domain controllers, specifically Event ID 4624.
Certificate Services
AllAuthenticated Users, by default, may collect certificate services data from Active Directory via LDAP. The majority of certificate services data is in the Configuration NC for the forest and collected with the AD Structure data.
The remainder of Certificate Services data may be collected from the Windows Registry.
Registry
SharpHound collects registry data for both certificate services and NTLM relay edges. The certificate services registry paths are on certificate authorities and domain controllers. NTLM relay paths are located on all Windows hosts. By default, onlyAdministrators may read the registry remotely. There are two methods to delegate remote registry access for least-privileged collection:
-
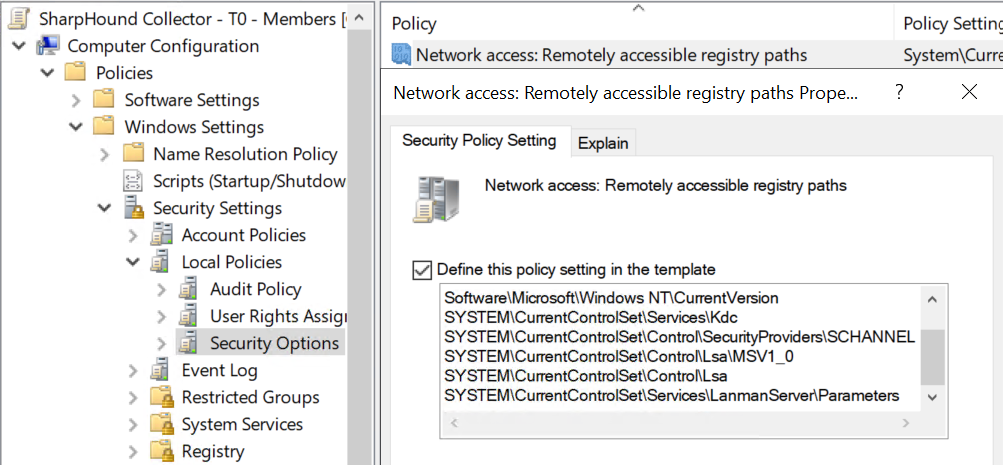
AllowedPaths / AllowedExactPaths exceptions: Create exceptions using the GPO setting Network access: Remotely accessible registry paths to allow
Authenticated Usersto connect to theRemote Registrynamed pipe at specific registry paths. Effective access is still governed by permissions on individual registry keys. -
Modify Remote Registry named pipe security descriptor: Alternatively, modify the default security descriptor on the
Remote Registrynamed pipe to grant explicit security principals read permissions to the entire registry. Permissions on individual registry keys still govern effective access.
CA Registry
When the AD CS role is installed in Windows, theHKLM\SYSTEM\CurrentControlSet\Services\CertSvc registry path is automatically added to HKLM\SYSTEM\CurrentControlSet\Control\SecurePipeServers\winreg\AllowedPaths. This creates a remote registry exception that allows Authenticated Users to query any keys and subkeys in this path, as long as they also are granted rights to read the key. Therefore, CA registry data is accessible to Authenticated Users by default when AD CS is installed.
DC Registry
For domain controllers, you can create exceptions by adding the required DC registry paths toHKLM\SYSTEM\CurrentControlSet\Control\SecurePipeServers\winreg\AllowedExactPaths using the GPO setting mentioned above. This will create an exception to the Remote Registry named pipe on the DC allowing Authenticated Users to read those exact key paths, as long as they also are granted permissions on the registry key DACL.
NTLM Relay Registry Paths
Registry paths for NTLM relay edges exist on all Windows hosts. By default, onlyAdministrators can access these paths remotely. To enable least-privileged collection, use Group Policy to add these specific paths to AllowedExactPaths. This grants Authenticated Users remote read access, following the same method described above.